News Block
Fullwidth Featured
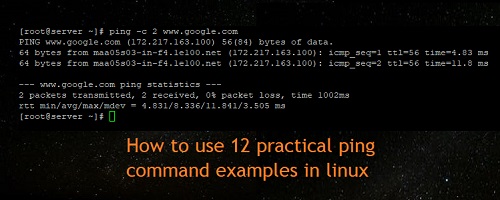
How to use 12 practical ping command examples in linux
Description Ping is a simple, widely used, cross-platform networking utility for testing if a host is reachable on an Internet Protocol (IP) network. It works by sending a series of Internet Control Message Protocol (ICMP) ECHO_REQUEST messages to the target host and waiting for an ICMP echo reply (or ECHO_RESPONSE). You can run a ping test in order to establish if your computer can communicate […]
How to disable SSH Root login in Linux
Description The root account is often the most targeted account by crackers via SSH under Linux. An enabled SSH root account on a Linux server exposed to a network or, worse, exposed in Internet can pose a high degree of security concern by system administrators. The SSH root account should be disabled in all cases in Linux in order […]
How To Create a Linux Swap File
Description We will explain swap space, and learn how to create swap space using a swap file in Linux: this is important in case we don’t have a swap partition created on the hard disk. Swap space/partition is space on a disk created for use by the operating system when memory has been fully utilized. […]
How to create a virtual HardDisk volume using a File in Linux
Description Virtual Hard Disk (VHD) is a disk image file format which represents a virtual hard disk drive, capable of storing the complete contents of a physical hard drive. It’s a container file that acts similar to a physical hard drive. The disk image replicates an existing hard drive and includes all data and structural features. […]
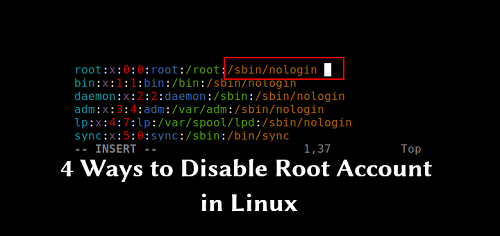
How to disable root account in Linux using 4 ways
Description The root account is the ultimate account on a Linux and other Unix-like operating systems. This account has access to all commands and files on a system with full read, write and execute permissions. It is used to perform any kind of task on a system to create/update/access/delete other users’ accounts, install/remove/upgrade software packages, and so […]
How to tweak password expiry using Linux Chage command
Description The chage command, lets you tweak user password expiry information Following is its syntax: chage [options] LOGIN And here’s what the man page says about it: The chage command changes the number of days between password changes and the date of the last password change. This information is used by the system to determine […]
How to copy files between hosts in a network using DCP
Description We often need to copy or share files over the network. Many of us are used to using tools such as rsync or scp to transfer files between machines. In this tutorial, we are going to review another tool that can help you copy files between hosts in a network – Dat Copy (dcp). Dcp does not require SSH […]
How to Downgrade RHEL/CentOS to Previous Version
Description If you have upgraded your kernel and redhat-release packages and you are encountering some issues. In this article, we will describe how to do downgrade RHEL or CentOS version to previous minor version. Note: The following steps will only work for downgrades within the same major version (such as from RHEL/CentOS 7.6 to 7.5) but not between major […]
How to Undo or Redo a Yum Install on CentOS and RHEL
Description One of the most important and useful feature added to YUM Package Manager (from version 3.2.25) is the ‘yum history’ command. It allows you to review a full history of yum transactions that have been run on a system. It shows the dates and times when a transactions were performed, whether the transactions succeeded […]
How to Run ‘sudo’ Command Without Entering a Password in Linux
Description In case you are running Linux on a machine that you normally use alone, say on a laptop, entering a password each time you invoke sudo can become so boring in the long run. Therefore, in this guide, we will describe how to configure sudo command to run without entering a password. This setting […]